1
Background and Overview
Despite the existence of the Biological Weapons Convention,1 the U.S. Department of State estimates that more than a dozen countries are pursuing the development of biological weapons.2 Of perhaps greater concern is the possibility that domestic or international terrorist groups could acquire or create biological weapons and use them against unprotected civilian or military targets. The anthrax letter attacks in 2001, in which the dissemination of a few grams of Bacillus anthracis spores in mailed envelopes resulted in the infection of 23 Americans and the death of 5, heightened Americans' sense of vulnerability—particularly coming as they did less than a month after the overwhelming attacks on the World Trade Center, in which nearly 3,000 people lost their lives.
In future events involving biological agents, early detection of an infectious agent cloud and early identification of individuals exposed will help to save lives. As shown in Figure 1.1, the earlier one can detect the release of a biological agent, the greater the options available for response. Thus, one speaks of detect-to-warn for the few minutes after an agent is dispersed during which it is still possible to take some action to minimize exposure. Similarly, one speaks of detect-to-treat for those hours or days following the release of agent when detection can still lead to early medical treatment and improved prognosis. At longer times, the benefits of detection are limited to assessment of the level of contamination and forensic identification of the source of the agent.
Today, technology can support the detection and identification of biological agents in time to pretreat patients before the onset of symptoms. In the future, greater emphasis will be placed on detect-to-warn—that is, the detection of an agent cloud in time to alter air movement within a building, treat the air before it reaches the occupants, or allow personnel to protect themselves with physical barriers to the hazards.
STATEMENT OF TASK
The Defense Threat Reduction Agency (DTRA) was created with the mission of reducing threats to the United States and its allies from nuclear, biological, chemical, conventional, and special weapons. Government policy makers, including DTRA, have identified rapid detection of attacks with biological
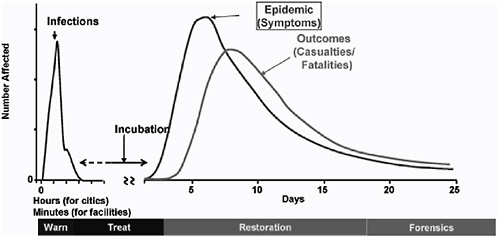
FIGURE 1.1 Notional time line for an anthrax attack showing the different detection regimes and requirements corresponding to different portions of the biological event. Detect-to-warn systems must respond in sufficient time to allow protective measures to prevent or minimize exposure of a significant portion of the at-risk population. Thus, detect-to-warn time lines can be on the order of hours for cities but only a few minutes or less for facilities.
agents as a priority, including the deployment of unobtrusive detect-to-warn sensor systems in key locations such as subways, airports, arenas, and military and government installations.
Accordingly, DTRA gave the committee four tasks:
-
Review the DTRA-specified requirements3 for detect-to-warn systems. Identify those requirements that will especially drive the detection concepts and architectures—for example, less than 1 minute detection times and continuous operations, with attendant implications for consumables and their costs—and understand to what extent, if any, these or related parameters, such as detection sensitivities, may be relaxed.
-
Consider examples of representative operational scenarios or architectures (to be provided by DTRA), which will be invaluable in putting these system requirements and trade-offs in context.
-
Identify specific sensor and sampling technologies that have the potential to satisfy system requirements, assess their state of development, and prepare a roadmap for further development to demonstrate required performance. If necessary, suggest temporary modifications to system specifications for interim development by FY2010 and fielding of best available technologies.
-
To the extent that the maturity of the above sensor and sampling technologies allows, identify critical materials, manufacturing technologies, and system design issues required to fabricate, validate, deploy, and support these sensor systems in diverse environments and enable the systems to meet requirements for low false alarm rates, low cost, compact size, light weight, low maintenance, and low power. The committee will also assess the current state of development of key enabling technologies and identify strategies and associated time lines for addressing major deficiencies.
For Task 2, the committee was given two basic scenarios of attack to consider: (1) the release of biological agent within a building or occupied space and (2) an outdoor release targeting an extended military installation.
SCOPE AND COMMITTEE APPROACH
The technologies for detection of biological agents considered by this committee are capable of providing different levels of information and may operate on different time scales. The functions performed by these technologies fall into three general categories:
-
Detection of the presence of biological particles (living or dead, pathogenic or nonpathogenic) in ambient air. Such detectors, which can provide a rapid response but may not be able to distinguish between hazardous agents and the nonhazardous biological background, are termed "nonspecific."
-
Tentative identification of specific biological agents or forms based on genetic, structural, chemical, or functional characteristics. Such detectors are likely to have a somewhat slower response than nonspecific detectors and must be preprogrammed to respond to anticipated biological threats.
-
Confirmation of the presence of specific types of biological agents. These technologies typically use multiple signatures for a more definitive identification of the species of agent but are likely to have the slowest response times.
To be useful, a detect-to-warn sensor system must be carefully integrated with the response capability. The response triggered by the sensor system—and the magnitude of the potential regret level (i.e., in case of a false alarm)—must be commensurate with the sensitivity and the false alarm rate. The ultimate goal is to keep a respirable aerosol out of the breathing space of humans who are at risk. A graded response for an indoor release scenario might first include a rapid, automatic reconfiguration of the HVAC system (which could be made imperceptible to the building occupants). Then, with more specific information about a biological attack might come a warning to don a protective mask or gear. Finally, a building or parts of a building complex might be evacuated. Too great a response to frequent false alarms will be too disruptive of normal human function and will likely result in the warning system being removed or ignored.
The value of the information provided by the sensor system will relate directly to the sensitivity, specificity, and false alarm rate of the assay system. Thus, the committee considered a variety of such characteristics as outlined in Box 1.1. Does the system sample enough air to find the threat organisms if they are present? Does it identify specific pathogens or simply detect an increase of respirable particles in the air?
To be of value, definitive information must be available in minutes to enable physical protective responses; hence DTRA's request for study of a one-minute warning sensor. In its deliberations, the committee focused on sensor technologies that could offer a one-minute response, although in some cases it considered detectors that could respond in 2 minutes or less since these could help save lives in some scenarios, even though this longer response time is less than optimal for many detect-to-warn applications. Depending on the type of sensor/detector system, the following sequence of processes might be required within this response time:
-
Collection of the sample,
-
Preparation of the sample for analysis,
-
Performance of the assay itself, and
-
Analysis and reporting of the results of the assay.
|
Box 1.1
|
Cost will be an issue, and some sensor systems will require more logistical support than others. Other cost-related considerations include the following: Will there be dual-use applications that might help justify the cost, or will the sensors only be of value for protection from bioterrorism? Will other countermeasures—for example, full-time air filtration systems or simply increased physical security—be more cost-effective than sensor systems?
This report considers the biological threat from intact agents such as bacteria and viruses (including genetically engineered or mutated agents) as well as from the molecular toxins produced by such organisms. A prioritized list of biological threat agents developed by the Centers for Disease Control and Prevention is shown in Table 1.1. The route of exposure considered in this report is assumed to be inhalation of aerosolized agents rather than skin exposure, contamination of food or water, or vector-borne transmission, because aerosols are likely to be the quickest and most effective means of exposing large numbers of people in the attack scenarios considered.
Aerosol particles between 1 and 10 micrometers are generally considered to be the most efficient for respiration into the human lung; however, the committee considered aerosols with particles as large as 30 micrometers because these larger particles can remain suspended in air for considerable times and are still reasonably effective in causing infection. Moreover, these larger particles are likely to be present in terrorist attacks that may rely on less sophisticated aerosolization methods.
TABLE 1.1 Centers for Disease Control and Prevention (CDC) Prioritized List of Biological Threat Agentsa
|
Disease (Organism) |
Agent Typeb |
|
Category Ac |
|
|
Anthrax (Bacillus anthracis) |
B |
|
Botulism (Clostridium botulinum toxin) |
T |
|
Plague (Yersinia pestis) |
B |
|
Smallpox (variola major) |
V |
|
Tularemia (Francisella tularensis) |
B |
|
Viral hemorrhagic fevers (filoviruses—e.g., Ebola and Marburg—and arenaviruses—e.g., Lassa and Machupo) |
V |
|
Category Bd |
|
|
Brucellosis (Brucella species) |
B |
|
Epsilon toxin (from Clostridium perfringens) |
T |
|
Food safety threats (e.g., Salmonella species, Escherichia coli O157:H7, Shigella) |
B |
|
Glanders (Burkholderia mallei) |
B |
|
Melioidosis (Burkholderia pseudomallei) |
B |
|
Psittacosis (Chlamydia psittaci) |
B |
|
Q fever (Coxiella burnetii) |
B |
|
Ricin toxin (from Ricinus communis—castor beans) |
T |
|
Staphylococcal enterotoxin B |
T |
|
Typhus fever (Rickettsia prowazekii) |
B |
|
Viral encephalitis (alphaviruses such as Venezuelan equine encephalitis, eastern equine encephalitis, western equine encephalitis) |
V |
|
Water safety threats (e.g., Vibrio cholerae, Cryptosporidium parvum) |
B |
|
Category Ce |
|
|
Emerging infectious diseases such as Nipah virus and hantavirus |
V |
|
a Available at http://www.cdc.gov. Accessed August 2003. b B = bacterium; V = virus; T = toxin. c Category A includes the highest priority agents that pose a risk to national security because they can be easily disseminated or transmitted from person to person; result in high mortality rates and have the potential for major public health impact; might cause public panic and social disruption; and require special action for public health preparedness. d Category B agents are the second highest priority and include those that are moderately easy to disseminate; result in moderate morbidity rates and low mortality rates; and require specific enhancements of CDC's diagnostic capacity and enhanced disease surveillance. e Category C agents are the third highest priority and include emerging pathogens that could be engineered for mass dissemination in the future because of availability; ease of production and dissemination; and potential for high morbidity and mortality rates and major health impact. |
|
The committee was asked to consider two scenarios of biological agent attack: an indoor release against the population of a building and an outdoor release against an extended military installation. As it considered these two scenarios, the committee recognized that buildings and facilities in which humans congregate will typically be easier targets for controlled attack than outdoor areas or military installations. Given the finite nature of enclosed spaces, minimal ambient ultraviolet light, and controlled air movement, a building will generally be an easier target than any open space. This conclusion is consistent with the experience of the anthrax letters, in which a small quantity of spores contained in a few envelopes resulted in exposure to personnel and required decontamination of several large office buildings and mail-handling facilities.
Conversely, an attack involving the release of a cloud of agent upwind of a military facility requires a much larger quantity of weaponized agent and must contend with exposure of the agent to ultraviolet light
as well as physical disruption by thermals or irregular air currents found in most large installations. At the right time of the day, more humans will be more vulnerable to a respirable aerosol threat in an enclosed space than outside, and indoor "weather" will almost always favor the attacker. Fortunately, however, enclosed spaces can be more easily provided with collective artificial protection than open spaces.
In view of the comparative simplicity and advantages to the attacker in the indoor scenario, as well as the richness of potential defensive responses, the committee focused most of its attention on detect-to-warn technologies for this scenario. However, it also considered the applicability of these technologies to the outdoor release scenario.
The committee found that Task 4 was the most challenging. This is because most of the technologies discussed in this report are not yet mature enough to support a discussion of specific materials, system design, or manufacturing issues. However, for the more mature technologies discussed, the committee attempted to highlight the key enabling technologies that will facilitate their deployment as effective detect-to-warn sensor systems.
Looking beyond the tasks assigned by DTRA, the committee also notes that the overall system to counter potential biological agent attacks must balance the advantages and limitations of detect-to-warn systems with other alternatives for protecting people. The best overall biodefense architecture will likely be a system-of-systems that includes not only detection systems but vaccines, therapeutics, collective protection, and other means of protecting personnel in facilities and installations. The analysis and balancing of these major defensive components is as essential as the pursuit of the promising detection-based architectures addressed in this report.
CONCLUDING THOUGHTS
Although the United States could some day be faced with such "designer" agents as bacteria containing genes coded for new virulence factors, viruses designed to target cell populations that they ignore in nature, or small, bioactive natural molecules not currently on any threat list, many of the principles discussed in this report will still apply 50 years from now. Infection and effective doses will remain the same. Most biological threats will be neither volatile nor dermally active; therefore, unless the agents are easily spread from person to person, the attacker will most often find it necessary to disseminate them in particles small enough to hang suspended in the air long enough to be inhaled by the intended victim in quantities large enough to cause disease.
For outdoor releases, weaponeers may achieve breakthroughs in ultraviolet protection that will allow stabilization of bacteria, viruses, proteins, and peptides, but the sun's heat will always spawn thermals and winds that move particles along with them, lending uncertainty to the intended cloud trajectory. Resting humans will still ventilate to obtain oxygen and expire CO2 in volumes ranging from 5 to 10 liters per minute. The cost and effectiveness of the sensors, the configuration of the facilities they protect, and the threat itself will continue to evolve. The most stable variable in this complex equation may be the human body and the life we seek to protect.
In the future, it will be necessary to make hard decisions regarding the protection of humans from biological threat agents. The purpose of this study is to assist homeland defense officials, hardware and policy developers, and, specifically, program managers within the Department of Defense to understand key state-of-the-art technologies, barriers, and enablers that might lead one day to effective biosensor systems for protection of buildings and installations.






