5
Information Assurance—Securing the Naval Command and Information Infrastructure
The Naval Command and Information Infrastructure (NCII), as a highly networked system, can be vulnerable to attacks against its communications and computing elements. These vulnerabilities would pose numerous risks for network-centric operations (NCO). This chapter discusses those vulnerabilities and possible approaches to minimizing the associated risk. While the risks are significant, the committee believes they are outweighed by the benefits in operational effectiveness to be gained from NCO. However, this does not mean that the risks can be ignored. Vigilance is required on the part of system designers, implementers, managers, and users to anticipate security vulnerabilities and to address them by technical or procedural means. Constant awareness that portions of the system may be compromised will help warfighters react appropriately to situations. Backup plans should be developed for the most likely compromise scenarios, and warfighters should be trained in these procedures.
This chapter briefly sketches the magnitude of the security problem in today’s systems; discusses the defense-in-depth strategy of prevention, detection, and tolerance; then, describes and assesses what the Department of the Navy is doing today for information assurance; and finally, identifies needed research and discusses some promising research programs that may produce needed technology.
5.1 INTRODUCTION
The Defense Information Systems Agency (DISA) estimates that there are 250,000 attacks on Department of Defense (DOD) computer systems every year.
Computer attacks against U.S. systems were up 22 percent from 1996 to 1997, according to a survey by the Computer Security Institute and the FBI. The most recent Computer Security Institute/Federal Bureau of Investigation survey, published in March 1999, confirms this trend.1 The 1999 report notes that denial-of-service attacks were reported by 32 percent of survey respondents, sabotage of data or networks was reported by 19 percent, and virus contamination was reported by 90 percent. Such attacks can be considered as the ordinary background activity that must be dealt with day to day. Some of this activity, when directed against DOD systems, might include information warfare actions to “prepare the battlefield” in the event of a need to interfere with U.S. activity in some future engagement. This is certainly of concern. Of even greater concern, perhaps, is the fact that the United States can expect targeted attacks on DOD systems to increase during hostilities. Both the threat and U.S. vulnerability can be expected to increase, especially as a result of our increased reliance on the technology that network-centric warfare represents. Vulnerability is increasing along with the increasing connectivity among military systems and between military and civilian networks. Thus, vulnerabilities in the networking technology or in any connected system can be exploited by anyone anywhere to penetrate and corrupt DOD systems.
Another source of vulnerability is the increased reliance on commercial products. Commercial security is neither designed nor intended to withstand information warfare attacks, and a large number of exploitable flaws in commonly used products are known to a wide community. Furthermore, the increased homogeneity that results from the nature of today’s commercial computer system marketplace leaves DOD open to attacks that can quickly affect a large percentage of its operations. DOD also depends on vulnerable commercial infrastructures such as telephone networks that, although highly reliable, were not designed to withstand information warfare attack. In addition, since the fleet’s operational networks and the naval force business networks will of necessity be interconnected, the shore establishment will provide many attractive opportunities for penetration and disruption that can extend to the fleets and even their tactical networks, as well as their essential shore support.
5.2 THREATS TO THE NAVAL COMMAND AND INFORMATION INFRASTRUCTURE
The United States can count upon its adversaries to search for ways to disrupt the NCII. An adversary may be able to perform analysis (such as traffic
|
1 |
Rapalus, Patrice. 1999. Issues and Trends: 1999 CSI/FBI Computer Crime and Security Survey. Computer Security Institute, San Francisco, Calif. Available online at <http://www.gocsi.com/prelea990301.htm>. |
analysis) to identify critical nodes and bottlenecks and may develop attacks on these points. Individual elements attacked to gain access or produce an effect may include links, nodes, people, software, and hardware. Because of the numerous connections, both sanctioned and unsanctioned, with the public Internet that are likely to exist within the NCII, penetration of even a low-level network may permit a skilled information warfare attacker to gain access to far more critical systems.
Because of the drawdown in physical assets and forces, an adversary can choose attacks that have magnifying effects, thus significantly degrading the ability of naval forces to conduct operations. For example, in a battle group, which now often consists of a nuclear-powered aircraft carrier (CVN), Aegis ships, and a nuclear-powered attack submarine (SSN), significantly reducing the communications or computing ability of even a single platform could severely impede operations. Marine Corps plans to project forces directly to objectives without building up ground infrastructure are likewise vulnerable to asymmetrical attacks by adversaries. Thus, adversaries who have no traditional military to engage U.S. forces with any hope of success may nevertheless reasonably expect that information attacks will succeed with little risk. The NCII will be an attractive target because naval forces and the success of their operations will depend on the continued correct functioning of the NCII. Such attacks could be on the NCII alone or could be part of an overall military plan of attack against U.S. forces that also includes traditional physical force.
In the future, naval forces will increasingly be faced with unconventional threats, which could include international criminal enterprises, terrorists, and sometimes also nongovernmental organizations (NGOs). These potential adversaries can rapidly and cheaply obtain IT-based capabilities as a consequence of the globalization of communication, information, and Internet technologies. Expertise in developing and using these technologies is cheap and available worldwide, which is evidenced by the large number of foreigners employed as technical system developers by the U.S. software industry. Even an economically disadvantaged state or nonstate organization can hire criminal elements or disaffected nongovernment members to complement and extend its own ability to attack the NCII. A near-peer power might aid and encourage rogue states or factions or terrorist groups in penetrating or disrupting the NCII.
Enemy ability to penetrate, exploit, and disrupt the NCII could be facilitated by insider support. A malicious insider could, alone or working with outside adversaries, seriously disrupt NCO. Nearly everyone in the naval forces may have access to the NCII, as may interoperable joint peers. As the number of people with access to the NCII grows, it is more likely to include individuals with a desire or motive to cause mischief or engage in sabotage, or who are susceptible to being co-opted by an adversary. Insiders with access to key systems or databases, such as system or security administrators, will be attractive targets for recruiting. One way to minimize this risk somewhat is to reduce
the scope of access and control available to any single individual and to require two- (or more) person control of key functions.
5.3 VULNERABILITIES OF THE NAVAL COMMAND AND INFORMATION INFRASTRUCTURE
5.3.1 Use of Commercial Products
The NCII, including its protection functions, will be built largely from commercial software and hardware computing and networking components. These commercial products contain numerous security vulnerabilities, which, as they are discovered, are routinely posted to frequently accessed Web sites (e.g., bugtraq). Attacks are developed against many of these vulnerabilities, and software tools to carry out the attacks are posted to hacker Web sites.2 Commercial security products are not built to withstand the strength of attack that can be expected for military systems but to provide protection appropriate for business operations. Known vulnerabilities in these security products, as well as attacks exploiting them, are also posted on the Web. Vendors may respond by issuing patches (which may take weeks) or correcting the problems in scheduled new product releases (which can take months), resulting in a period of exposure during which procedural workarounds must be employed to reduce risk as far as possible. Many system operators may not be aware of the vulnerabilities that have been discovered in the products they are using or of the availability of procedural workarounds or patches.
The high rate of release of new products and product upgrades means that at any given time there will be no common software configuration across the NCII. With each new product and product release comes the need to keep up to date on product vulnerabilities and fixes. In addition, policy must be generated about acceptable and safe product configurations, and these configurations must be monitored and enforced across the NCII, because failure to do so would result in unnecessary exposure to vulnerabilities.
Additionally, because so much commercial software, including that from the well-known vendors and manufacturers, is produced overseas or domestically using overseas or green-card labor, it is possible for an adversary to plant or co-opt people in product development positions and have them attempt to include malicious triggerable code in commercial products that will be used in the United States and by the DOD. Such hidden features can easily go undetected by the vendor.
|
2 |
See, for example, <http://www.hackershomepage.com/index.html> and <http://www.hackcity.de/programme.shtml>. |
5.3.2 Reliance on Unclassified or Low-classification Information for Sensitive Functions
Sensitive NCII functions may rely on unclassified open source information. Such information sources are vulnerable to tampering and insertion of bad information by malicious entities before the information enters the NCII.
5.3.3 Outsourcing and Contract Personnel
Outsourcing of certain functions and the resulting introduction of contract personnel who require access to the NCII increase the possibility of introducing individuals who can cause damage or collaborate with hostile outsiders.
5.3.4 Joint and Coalition Member Access
To carry out joint and coalition operations, it may be necessary to give NCII access to joint and coalition personnel. This increases the likelihood of having insiders with motivation to cause damage. This population may also have a much poorer understanding of security, thereby decreasing general security awareness and vigilance among the user and operators of the NCII.
5.3.5 Connectivity to Public Networks
The NCII will have connections to the Internet and the Web to gain access to useful information, such as weather, environmental, news, and personal and recreational information. Attacks on these public databases may hinder the NCII. This connectivity also exposes the NCII to viruses and other information warfare weapons in data and code that enter the NCII. Also, NCII users might download arbitrary code, which could be infected with viruses or worms that could spread and cause damage within the NCII. It is also possible for an adversary to disguise hostile code, such as viruses, in attractive, free, software that NCII users may be tempted to download from the Web, thereby compromising the NCII.
Another risk of connecting to public networks is the increased use of mobile code, for example to implement so-called intelligent agents. With mobile code, users may be importing code into the NCII without being aware of it. While vendors have been adding security capability into the tools and languages commonly used to build mobile code (e.g., Java), such protections are not commonly in use on the Web.
Connectivity to public networks may also allow adversaries to observe the Department of the Navy’s activity on the public networks and infer information about the Navy Department’s operations and plans. To the extent that the NCII uses public networks to convey encrypted classified information, an adversary will be able to perform traffic analysis and infer useful information, including
information that will help it to understand useful targets for denial-of-service attacks. In the DOD Eligible Receiver exercise in 1997, red team attackers penetrated sensitive networks by first attacking less sensitive networks to which they were connected.
5.3.6 Homogeneous Technology
Market forces and consolidation within the computer industry have meant that a few brands of software and hardware are ubiquitous. The NCII will also be largely homogeneous, with common products in use everywhere. Such homogeneity leads to widespread common vulnerabilities that can be exploited by common attacks. Large-scale networks of such systems are particularly vulnerable to virus attacks that can spread rapidly, because every system is vulnerable to the same virus. The devastating consequences of disease that are possible with homogeneous populations have been long recognized by the agricultural industry, which uses the strategy of crop diversity to limit the spread of disease and its consequences. For information networks, the availability of diverse implementations of common protocols and standards could help provide robustness, although such availability is not expected anytime soon.
5.3.7 Vulnerabilities of Tactical Networks
Tactical networks have particular vulnerabilities in addition to those they share with conventional wired networks. Tactical networks are subject to spoofing, jamming, and interception through the air. An adversary can launch a spoofing attack by attempting to introduce false information into a tactical network through false radio transmission. Through-the-air transmissions are vulnerable to jamming by suitably located and directed enemy transmissions. Because tactical transmissions are through the air, they may be subject to interception with greater ease and at a greater distance than those carried over wired networks. An adversary who intercepts U.S. radio signals can attempt to gain an advantage in several ways. It can try to gain intelligence about U.S. forces’ status and intentions by reading the data; it can make inferences about present and future activities by noting the source, destination, and volume of radio communications (that is, by performing traffic analysis); and it can geolocate the transmitting platform.
In addition, because tactical networks may be within reach of enemy forces, end instruments are subject to terminal capture. Enemy capture of a network node means that the enemy is inside a naval network. If this seems a remote possibility, it should be remembered that the naval tactical networks will include Marine Corps ground networks and will be closely linked into those for the Army. A tactical node can be overrun as a result of an action as simple as the capture of a single wheeled vehicle. Enemy capture of a functioning network
node could take some time to notice and respond to, during which time a great deal of damage could be inflicted, some of which might last far longer than the node itself. For instance, an enemy could spoof the common tactical picture, adding fictitious elements to it, and could also engage in various types of network denial-of-service attacks.
Another problem would arise if the United States were unwilling to share its cryptographic apparatus with coalition partners. Either it would not fully benefit from their data or it would risk the introduction of corrupted data.
5.3.8 Interconnection of Networks of Different Classifications
The NCII will require the interconnection of networks of different classifications, so that information contained in low networks is available to high networks and also so that appropriately sanitized high data can flow to low networks. There is a risk that unless extreme care is taken in the design and implementation of the boundary controllers that connect such networks, high information could leak into low networks. If there is a hostile insider or hostile code on a high network collaborating with an entity on a low network, high information could be sent covertly using steganographic means. There are no means of detecting such an information flow. Man-in-the-loop security release stations are useless against such a covert flow but pose their own risks, since approving information for release is a tedious task and the operator can routinely and unthinkingly approve the release of information that should not be released. In addition, there is a risk that low code and data that enter a high network can be maliciously tampered with in the low network to corrupt high databases or to introduce malicious code into high networks.
5.3.9 Interference with Critical Functions
The indiscriminate interconnection of strategic and tactical information networks with mission-critical networks (e.g., those used for air defense) can have undesirable consequences. First, such interconnection exposes these critical functions to tampering from a large interconnected population. Second, the bandwidth and computing resources for those critical functions may not be available when needed owing to competition from other users and applications. And third, unanticipated interactions between the interconnected networks may result in the failure of critical functions; these interactions can be particularly difficult to diagnose and correct.
5.4 DEFENSE IN DEPTH
Experience has shown that many successful attacks on DOD systems are not detected. In these attacks, an intruder may make surreptitious use of a
penetrated system; may silently steal data or gather intelligence; may plant malicious code, perhaps for future use; may alter data, perhaps to lead the user or system to an erroneous decision; or may interfere with or degrade system operation. Such attacks could make systems unusable, degrade performance, lead commanders to make poor decisions due to faulty data, leak valuable secrets, or leave behind code that could provide continuing backdoor access or be activated at the occurrence of a predetermined event to take obstructive action. It is clear that such attacks cannot be prevented or even reliably detected. Thus, in addition to erecting access barriers and deploying detection systems, the Department of the Navy must discover how to design its critical systems, using commercially available components, so that they can be relied on to provide continuous correct operation in situations in which they are successfully attacked.
The notion that it is not possible to discover all vulnerabilities and use this information to guide a protection strategy is contrary to current thinking in DOD, where the emphasis is on discovery of vulnerabilities, so that appropriate protections can be placed to counter them. This popular vulnerability discovery approach puts protections in place only where there are known vulnerabilities. But because there is no way that all vulnerabilities can be discovered, such an approach will leave the system unprotected from its unknown exploitable vulnerabilities, which, if discovered at all, would be found out only during the operational lifetime of the system. This is a dangerous situation, because an adversary may well discover and exploit vulnerabilities that are still unknown to the Department of the Navy. In fact, the situation is asymmetric, because a determined adversary can decide which part of the system it wants to manipulate or exploit, purchase the commercial products that are used in that part of the system, and spend many months deconstructing these products to discover vulnerabilities that can be profitably and surreptitiously exploited. While such an approach is clearly affordable by an adversary, it is not affordable as a defense, since the defender would have to perform a costly analysis for every system component, whereas the adversary can pick and choose its focus of attack.
The Department of the Navy must operate on the assumption that any component of any system may have unknown security vulnerabilities that could be exploited by an adversary. Even the security protections put in place may contain such unknown vulnerabilities. With this in mind, the Department of the Navy will have to add redundant, independent security mechanisms and assume that not all attacks can be prevented, although there must be some means to detect attacks that are successful. Even more so, the Department of the Navy must recognize that its detection technology is far from perfect and that there will be successful attacks that are not detected. Thus, naval systems must be designed, to the extent possible, to be able to continue functioning despite the presence of an attacker. Appropriate strategies such as confusing an attacker who has successfully penetrated naval systems must also be developed.
Defense in depth is a threefold strategy that emphasizes prevention, detec-
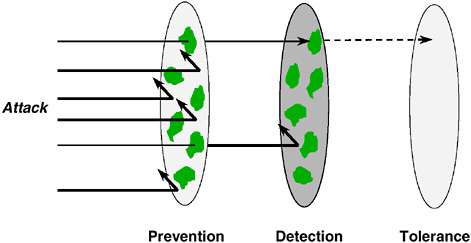
FIGURE 5.1 Defense in depth. SOURCE: Modified from a figure by Sami Saydjari shown during a briefing to the committee, DARPA, Arlington, Va., May 19, 1999.
tion, and tolerance (Figure 5.1). But today such a strategy cannot be completely implemented because of technology shortfalls at each level of the defense-in-depth strategy.
Many people in DOD and the Department of the Navy use the term “defense in depth” to mean what the committee calls a layered defense (discussed in Section 5.4.1.1). Here, a layered defense is considered to be part of a defense-in-depth strategy.
5.4.1 Prevention
To be affordable, naval networks and systems must use commercial products and services to the extent feasible. These products and services were not built to meet the security demands of network-centric operations. They generally have many known security vulnerabilities, and new vulnerabilities are discovered throughout their lifetimes. Because commercial products are so large and complex, it is not generally possible to discover all the vulnerabilities in advance, no matter how much testing is performed. Thus, all components must be treated as vulnerable, and the systems that use these components must be designed bearing in mind that there may be security vulnerabilities in any system component. Even when security functionality is designed into commercial products and services, this security is generally weaker than that required for naval needs.
This points to the need to be able to design systems built from insecure components and services so that the systems are secure against threats to naval forces. While the security research community has long recognized the need for
viable approaches to building secure systems from insecure components, very little is known about how to do this, and secure system design remains an ad hoc, poorly understood discipline.
5.4.1.1 Layered Defenses
The committee does not discourage the Department of the Navy from performing vulnerability assessments. The more one knows about a system, the better. The point is not to rely on vulnerability discovery to guide the protection strategy (this is sometimes referred to as a penetrate-and-patch strategy). A better and safer strategy is to assume that every system component contains unknown security vulnerabilities that can be exploited by an adversary. Where to place protections against such unknown vulnerabilities will depend on an analysis of the consequences if any of these unknown vulnerabilities are exploited. In designing protections, it must also be kept in mind that the protections themselves can contain unknown, exploitable vulnerabilities.
Because every system component, including the protection components, must be assumed to contain unknown, exploitable security vulnerabilities, a layered defense strategy must be employed. The idea here is that protections are employed to counter known and unknown security vulnerabilities in the system. Barriers to attack can be employed to counter many types of potential vulnerabilities; however, a single barrier should not be relied on to repel a determined adversary. Because these protection components themselves may contain vulnerabilities (both known and unknown), additional layers of protection must be employed. Such a layered defense reduces the likelihood that an attacker can find an exploitable vulnerability, because for this to happen, not only must the original system contain a vulnerability, but each successive protection layer must also be flawed. Having several layers of defense increases the difficulty for the attacker. Each additional layer increases the odds for the defense and reduces the odds for the attacker. Thus, a layered defense helps to provide additional defenses even if a particular protection mechanism is subverted.
5.4.1.2 Malicious Insiders
One important source of vulnerability is the malicious insider. Working alone or with outside adversaries, a malicious insider could seriously disrupt network-centric operations. Monitoring user activities is another risk-reduction technique. Software that tracks downloading and checks for authorization; required use of biometric as well as password identification for users; and continuous record keeping of user log-on and log-off times with subsequent pattern analysis can all add a measure of security and potentially increase the likelihood of detecting malicious insider activities. All of these steps, especially many cascaded together, will add complexity and delay in many system functions. A
balance will have to be struck between reducing risk and supporting functionality. The NCII must be able to accommodate ad hoc adjustment by commanders to account for shifting degrees of urgency and penalty for error, while sustaining some essential safeguards.
5.4.1.3 The Limitations of Commercial Product Assessments
Many in the DOD are concerned about the widespread use of commercial products in DOD systems and the potential vulnerabilities to the missions that rely on the use of these products. Some of these people advocate that the DOD institute a function that would evaluate commercial products to discover their vulnerabilities, so that appropriate defenses or workarounds can be developed. It will probably not be possible to do a good job of this, no matter how much testing is performed, because of the size (lines of code) and complexity of these products.
If an adversary were to plant or co-opt people in product development positions and have them insert malicious, triggerable code into commercial products, such hidden features could go undetected by the vendor’s quality assurance and testing. Detecting such codes would be even more difficult for DOD, which has access only to the object code of these products, despite the advanced reverse-engineering capabilities present in certain parts of DOD. The likelihood of such a scenario can be assessed in light of the fact that it is fairly common for popular programs to have undocumented features that survive in final product releases without the knowledge of the product manager (e.g., special key sequences to bring up hidden games or photographs of the developers). The functionality of these products is simply so extensive that unused hidden functionality is highly unlikely to be discovered by any software evaluation techniques.
The committee believes that the Department of the Navy should collect as much information as possible about products it has in widespread use. This information can be collected from an in-house evaluation (of both functional and security aspects) as well as from evaluations performed by other organizations. For example, the National Institute of Standards and Technology has established common criteria for products as well as a common evaluation methodology, and product evaluation information is available for some products.3
DARPA’s Information Assurance Science and Engineering Tools program4 is attempting to develop assurance metrics and evaluation tools for systems.
|
3 |
National Institute of Standards and Technology. 1999. Common Criteria Project. Gaithersburg, Md., November 1. Available online at <http://csrc.nist.gov/cc/>. |
|
4 |
Skroch, Michael J. 2000. IA Science and Engineering Tools. DARPA, Arlington, Va., January 1. Available online at <http://iso.isotic.org/Programs/progtemp/progtemp.cfm?mode=342>. |
However, experience shows that such an endeavor cannot be expected to have a high likelihood of success, for the reasons outlined above, although the committee expects the program to advance the state of knowledge, if not of practice.
DARPA’s Information Survivability program5 developed a tool that can help identify places in source code which, if flawed or tampered with, could result in a security breach or program failure. Because it is generally difficult to obtain source code for commercial products, a similar tool is being developed to operate on object code. These early investigations, using approaches borrowed from the software reliability community, may help vendors build better products and help the Department of the Navy understand the potential vulnerabilities of those products.
5.4.1.4 The Limitations of Red Teaming
“Red teaming” is commonly advocated within DOD as a way of discovering and fixing vulnerabilities. A red team typically takes on the role of an attacker, either with or without the knowledge of the system operators, in order to discover whether available countermeasures for known attack methods are implemented on the system. It is frequently mentioned as the primary way of establishing security in a system. Red teaming is not, however, intended as a means of discovering vulnerability or even as a primary method for fixing discovered security flaws. The value of red teaming is twofold. First, it is arguably the best tool for raising security awareness in an organization. Most red teams discover known security holes for which known fixes, configurations, or patches have not been applied or where compensating security procedures are not in effect or not being enforced. By exploiting these weaknesses, they generally are able to demonstrate that they could have done significant damage to the system’s resources and could have had significant mission impact. This is useful in attracting high-level attention to security issues. Second, red teaming is useful for ensuring that correct security configurations are maintained for the system. This type of red teaming can be carried out periodically by the system’s security staff. Because red teaming is very useful in these two ways, the committee encourages the Department of the Navy to continue and increase its regular practice of red teaming.
But red teaming is not a good way of discovering vulnerabilities. First of all, most red teams use only known, published attacks that exploit known vulnerabilities. So the knowledge gained is not new, but pertains only to the specific installation. (This also means that a red team exercise is too weak to be
a useful “final exam” for systems, as is advocated by some in the DOD.) Second, red teaming occurs only after a system has been designed, implemented, deployed, and operated for some time. Even if vulnerabilities were discovered by red teaming, it is too late in the system life cycle to effectively and affordably correct them. Some organizations have put forth the notion of red teaming a system design, which would help to discover security problems early and correct design problems that are not correctable once the system is built. Red teams, or penetration teams, could also be employed to try to discover ways of attacking system or component implementations. This approach would not use known attacks, since there would not yet be any known attacks against these new components, but it would add a security dimension to component and system testing. The committee strongly advocates security red teaming of both designs and implementations before new systems are put into use.
Red teaming should not be thought of as a security panacea or as the primary way of achieving system security. At best, it amounts to reliance on a penetrate-and-patch strategy as the main mode of system defense. Penetrate and patch does not work as a defense, because it can never be expected to discover all system vulnerabilities. Most seriously, it may not uncover the unknown vulnerabilities that could be exploited by an information warfare adversary. Instead, it should be regularly applied as a consciousness-raising tool and for maintaining compliance with correct security configurations in deployed systems.
5.4.2 Detection
Even a layered defense will not eliminate the possibility of successful attack. The Department of the Navy must employ methods to detect attacks that are not successfully repelled. Intrusion detection technologies are commercially available, although these have well-known shortcomings, such as a very high false alarm rate and the ability to detect only a limited class of attacks on a limited set of system components. Specialized attack types on DOD-unique system components will certainly not be detected, and neither will application-specific attacks. Even generic attacks on operating systems and networks cannot be reliably detected. Moreover, today’s intrusion detection products generally can detect only attacks that have been seen before, whereas an information warfare adversary can be expected to be developing an arsenal of new attacks that current intrusion detection systems cannot anticipate.
To carry out joint and coalition operations, it may be necessary to give NCII access to joint and coalition personnel, increasing the likelihood of insiders with motivation to cause damage. Intrusion detection should also be directed at detecting malicious insiders. This problem is particularly difficult because insiders may not have to break in or circumvent access controls, so that detection approaches that rely on detecting evidence of such breaches will not be effective against them.
Although DARPA has a sizable research program to develop new intrusion detection technologies, even these still have a long way to go to reduce false alarm rates to acceptable levels, increase detection rates, and detect more types of attack. A joint evaluation on intrusion detection was conducted in 1998; MIT Lincoln Laboratory (MIT/LL; Lexington, Massachusetts) conducted the off-line evaluation, and the Air Force Research Laboratory (Hanscom Air Force Base, Bedford, Massachusetts) did the real-time evaluation.6 Conducted under the sponsorship of DARPA and the Department of the Air Force, the evaluation showed that the DARPA technology reduced false alarms by orders of magnitude and increased detection rates roughly fivefold. Yet this same evaluation also showed that false alarm rates are still too high, especially when multiplied across a very large system, as would be the case in network-centric operations. The evaluation also showed that detection rates and the number of attack types detected must still be increased significantly. The evaluation showed that most detection techniques are good at detecting certain attack types and not so good at detecting other types. Thus, a reasonable detection strategy is to employ a variety of detection techniques. Figure 5.2 compares the results of the best combination of research prototypes with the results from a key word baseline system that is representative of the many commercially available intrusion detectors that use string matches on key words as the detection method.
The DARPA/Air Force Research Laboratory (AFRL) evaluations were intended to drive improvements in the research prototypes. A second round of evaluations was conducted in 1999, and a third is planned for 2000.7 The results of the 1998 evaluation were reported in the July 1999 Communications of the ACM (Association for Computing Machinery).8 The 1998 evaluation used Unix audit logs and Transmission Control Protocol (TCP) dump data, which are the sources of data for typical commercial intrusion detection products. The 1999 and 2000 evaluations will increase the number of data sources used in the evaluation. The methodology used employs a live evaluation of the intrusion detection research prototypes on a network at MIT/LL using simulated data similar to data collected at Air Force bases. MIT/LL generated large amounts of realistic background traffic similar to observed and collected traffic at the bases. This
|
6 |
Lippmann, Richard, Marc Zissman, David Fried, Sam Gorton, Isaac Graf, David McClung, Dan Weber, Seth Webster, and Dan Wyschogrod, “1998 DARPA Intrusion Detection Evaluation Plans– 2/98,” a briefing at the DARPA PI meeting, February 3, 1998, Annapolis, Md. Available online at <http://www.ll.mid.edu/IST/ideval/docs/9802-pi/index.html>. |
|
7 |
Zissman, Marc A., and Richard P. Lippmann. 1999. DARPA Intrusion Detection Evaluation. MIT Lincoln Laboratory, Lexington, Mass., December 22. Available online at <http://www.ll.mit.edu/IST/ideval/>. Also, personal communication from Richard Lippmann, MIT Lincoln Laboratory, February 18, 2000, regarding the 1999 and 2000 evaluations. |
|
8 |
Durst, Robert, Terrence Champion, Brian Witten, Eric Miller, and Luigi Spagnuolo. 1999. “Testing and Evaluating Computer Intrusion Detection Systems,” Communications of the ACM, Vol. 42, No. 7, July, pp. 53-61. |
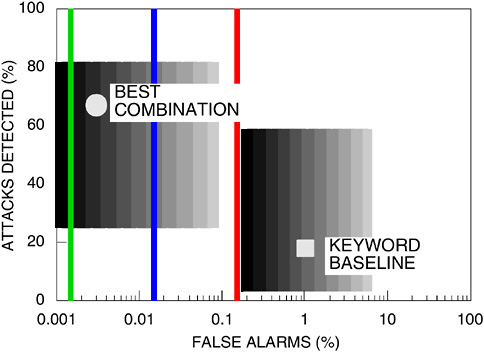
FIGURE 5.2 Comparison of research prototypes and keyword baseline for intrusion detection.
SOURCE: Modified from: (1) Lippmann, Richard, Robert Cunningham, Dave Fried, Isaac Graf, Kris Kendall, Seth Webster, and Marc Zissman. 2000. “Results of the DARPA 1998 Offline Intrusion Detection Evaluation,” in Proceedings of the 2nd International Workshop on Recent Advances in Intrusion Detection [workshop held September 7-9, 1999], Center for Education and Research in Information Assurance and Security (CERIAS), Purdue University, West Lafayette, Ind., forthcoming. (2) Lippmann, Richard. 1999. “Best Combination System from 1998 Evaluation Compared to Keyword Baseline,” Summary and Plans for the 1999 DARPA Evaluation, January 28. Available online at <http://www.ll.mit.edu/IST/ideval/summary-html-dir/>.
background traffic was used to measure false alarm rates of the intrusion detection prototypes. AFRL and MIT/LL also created the largest known collection of automated attacks with signatures, for both audit trail and TCP dump data sources. These automated attacks were used to evaluate the ability of the research prototypes to detect known attacks. In addition, the evaluation measured the ability of the research prototypes to detect types of attacks never seen before. To do this, AFRL and MIT/LL developed a set of new attacks. This is the first evaluation that allowed side-by-side comparisons of different detection methods for both false alarm rate and detection rates against both known and previously unknown attack types. The researchers were also provided with extensive train-
ing and testing data sets and performed self-evaluations. Some of them have begun to publish their results in conference proceedings and technical journals.
5.4.3 Tolerating Attacks
Because intrusion detection technology cannot be depended on to detect all successful attacks, the third aspect of defense in depth is to design systems so they will be able to tolerate attacks. This means that systems must be able to continue to operate despite a successful attack, by means of attack containment as well as strategies to minimize damage. Today very little is known about how to build a system this way. DARPA has launched a new research program in intrusion tolerance to begin to explore this area.
5.5 ASSESSMENT OF CURRENT INFORMATION ASSURANCE ACTIVITIES
This section gives a general assessment of the state of practice of information assurance. The assessment also applies to the Department of the Navy and briefly discusses specific naval activities. It suggests near-term actions the Navy Department can take to begin to improve its information assurance position.
Like the DOD in general as well as the country at large, within the Department of the Navy available security technologies are not being used widely enough.9 Even when these are installed, adequate procedures are needed to maintain correct and secure configurations. While this task can be partially automated, a large part is still labor-intensive, requires strict adherence to procedures, and relies for its success on the awareness and commitment of the vast majority of users. A procedural or technical means should be developed and used to verify that the mandated security functionality is correctly applied in all naval systems. Moreover, security is not a part of the readiness assessment of the forces, so that it is not given as high a priority as other considerations, and forces are considered ready even when they cannot defend their information-based operations (on which the success of their missions may well depend).
The Department of the Navy has no coherent plans for information network security in its tactical networks. Security should be part of the foundation of an information network architecture—it is extremely difficult to add after the fact. Years of work have gone into adding security to the Internet, after the fact, but the results are still far from satisfactory. Web sites continue to be hacked and intruders continue to gain access to poorly protected computers. The Depart-
ment of the Navy should take great care that its tactical networks are at least as secure as those provided by commercial vendors.
The difficulty of achieving security is evident when one considers that there are no commercial solutions to many security problems, and that current commercial technology (e.g., intrusion detection, firewalls, and authentication systems) leave much to be desired.
5.5.1 Current Naval Activities
The Department of the Navy has issued guidance for how to secure information systems.10 It cannot be assumed, however, that all or most naval locations are following this guidance. Moreover, the guidance is only technical. Where no technical solution exists, or the solution is inadequate, additional guidance is needed on procedural security methods. One shortcoming of this guidance is that it may suggest too much reliance on some immature and unproven security technologies. For example, intrusion detection systems are recommended, but their significant shortcomings are not discussed. The guidance also recommends that the so-called “network intrusion detectors” (meaning detectors that look for a set of known intrusions from data sniffed from a communications line) can be used at certain interfaces instead of network firewalls. The document provides guidance for about five years into the future. It is very conservative in its projections and barely considers whether any new technology for security will be available. For instance, the data encryption standard 3DES is recommended for the indefinite future, although it is expected to be replaced by a much better standard in a few years. As another example, the guidance does not consider that there may be new types of intrusion detection available in the next five years. Generally, this guidance document is a good place to get started, and it refers to other documents for more complete guidance in some areas, such as how to configure Unix for security.
The Department of the Navy, and particularly the Naval Research Laboratory (NRL), is engineering solutions for IT-21 that include firewalls; virtual private networks; multilevel security for coalition operations and tactical/ nontactical (TnT) interaction; intrusion detection; synchronous optical network (SONET)/asynchronous transfer mode (ATM) security; Class C2 operating systems; secure Web protocols such as Secure Socket Layer (SSL); virus detection; some authentication in routing, switching, and domain name service; and mail guards. Security architectures are being developed to use these protections in a layered defense strategy. Protections and intrusion detection are the first two components of defense in depth.
The NRL also performs security certification and accreditation, develops embeddable and programmable cryptography for naval cryptographic replacement needs, and performs highly regarded security research.
The Department of the Navy is developing a Navy/Marine Corps intranet (N/MCI) to link naval ashore assets, which is expected to be operational by the end of CY2001. The N/MCI is expected to include commercial virtual private network (VPN) technologies that allow private interactions among identified communities across the common network. Protections for the N/MCI will also include conventional multiple levels of firewalls, intrusion detection, encryption and a public-key infrastructure, incident response teams, red teams, physical and procedural controls, and awareness and training programs. The N/MCI will provide access to naval, joint, coalition, and public Internet sources of information and reliance on a multiplicity of databases and sources, most outside the direct control of the naval forces. Much of the system, including its protection mechanisms, will be implemented with commercial software and hardware products and services. There will be widespread outsourcing of installation, support, and upgrade of enterprise hardware and software.
The Department of the Navy, like the rest of DOD, uses cryptography to separate classification levels in its networks. This allows information of different classifications to share some of the same physical network elements, such as routers. In effect, each classification has its own virtual network. One purpose for the encryption is to protect the classified information from being read by unauthorized parties. However, an additional reason for the encryption (and for classification in general) is to provide a degree of confinement, that is, to minimize the extent of exposure if someone gets access to classified information. The cryptography is good for this purpose only as regards damage from inappropriate information release. Because of the shared network elements, other types of damage are not confined to a given classification. Thus, for example, an adversary who gains access to the unclassified portion of the network may be able to use this access to perform denial-of-service attacks or other manipulations on the higher classified virtual networks by attacking or manipulating the shared elements. These shared physical elements form points of vulnerability, in that even if an attacker could not recover classified data, it could still use such points to manipulate the network.
5.5.2 Risks of Connectivity
Sensitive NCII functions may rely on unclassified, open source information. Such information sources are vulnerable to tampering and insertion of bad information by malicious entities before the information enters the NCII. Countermeasures could include integrity checks on the incoming data that alarm when the data fall out of expected or usual bounds, and comparison of data from a variety of sources to avoid overreliance on unique sources. It may also be
possible to maintain a pedigree for the data that would record information about its source, which could be used if the data are discovered to be tainted. These pedigrees could, for example, help to locate other data that might also be tainted and could be helpful in backtracking to discover the source of the tainted data.
Connectivity to external networks, including the open Internet, exposes the NCII to viruses and other information warfare weapons in data and code that enter the NCII. Also, NCII users may download arbitrary code, which may be infected with viruses or worms that can spread and cause damage within the NCII. The NCII should employ the most recent virus detection software on all its systems, including its end user systems, and NCII operators must be vigilant about ensuring that the correct versions are installed and the detection tables are kept up to date. Policies about importing code should also be developed and enforced. It may also be desirable to disallow mobile code (applets) until adequate security solutions are available.
5.5.3 Security for Tactical Networks
Four major vulnerabilities of wireless communication—spoofing, jamming, interception, and terminal capture—are considered here, along with a general discussion of security and lower-layer tactical radios.
5.5.3.1 Spoofing
An adversary who introduces false information into a tactical network may degrade the performance of that network. Such spoofing can be prevented in all cases but one by the use of appropriate cryptographic apparatus at each end of the transmission. The exception occurs when a terminal is captured; reliable methods of personal identification have long been sought, but few, if any, are available for field use.
5.5.3.2 Jamming
There are two main techniques for resisting communications jamming—signal processing and antenna directivity—and a combination of them is often appropriate. By the use of spread-spectrum waveforms, spectrum (but not necessarily data rate) can be traded for jam resistance. If spectrum is limited, data rate is compromised at some point, but trades between data rate and resistance are possible, and, with programmable modular radios, these trades can be made dynamically.
Spread-spectrum options and their antijam performance are well understood. However, most calculations of processing gain—the degree of jam resistance afforded by the waveform—assume that the transmitter and receiver are already synchronized. Designers must take care that the synchronization pro-
cess itself is not a fruitful jamming target. They must also ensure that their waveforms are not vulnerable to signal-specific techniques such as a jammer following the instantaneous frequency of a slow hopper and concentrating its power there.
Of the existing systems, JTIDS provides robust protection against jamming at moderate data rates and SINCGARS provides some protection against jamming at low data rates. Both systems use nondirective antennas to simplify their use in information networks involving multiple moving units.
Antenna directivity helps defeat jamming in two ways: directive-transmit antennas send more signal power to the receiver than would omnidirectional antennas, and (in most scenarios), directional-receive antennas receive less jamming power than would omnidirectional antennas.
Directional antennas at both ends of a link are appropriate for point-to-point transmission, and directional antennas at diverse locations can be pointed at a single broadcast transmitter. However, implementing a datalink architecture with directional antennas in which every participant can hear every other participant directly would require multibeam antennas on every node. This is the expensive solution adopted for the CEC data distribution system. Prospects for cheaper multibeam antennas are discussed in Chapter 6.
5.5.3.3 Interception
An adversary’s attempt to read intercepted radio signals can be foiled by effective encryption. Traffic analysis can be countered by some mixture of having every unit transmit all the time—even when they have nothing to say—and of encrypting packet headers so as to prevent destinations from being deduced. Contrary to first impressions, the transition to network-centric operations will probably make traffic analysis more difficult. Current transmission security devices will likely be augmented with end-to-end encryption, which, like current network encryption system (NES) devices, hide the network addresses. Furthermore automatic relaying of traffic will tend to mix traffic streams and help disguise the actual sources and destinations of traffic flows. That said, this area does require careful analysis and design.
Enemy interception of radio signals for the purpose of performing geolocation, however, can be forestalled only by making the signals hard to detect. There are two trustworthy means of accomplishing this. Directional transmit antennas pointed at the intended receiver and away from areas where adversary interceptors might be located constitute one way. The other is to use a spread-spectrum coding. Less reliable methods include concealing the transmission in the frequency or time shadow of other transmissions, and using infrequent, short-duration signals in the hope that the adversary has not deployed intercept apparatus capable of detecting such signals. It is inevitable that individual platforms will perform more radio transmissions as they become full partici-
pants in NCOs. This effect is most pronounced in developing the common tactical picture (CTP), because each platform will need to transmit its geolocation relatively often in order to be properly located within the CTP. There is no obvious answer to this problem beyond making the signals hard to intercept.
Although some spread-spectrum modulations are equally useful for overcoming jamming and preventing interception, they cannot do both simultaneously. To overcome jamming, the signals would have to be sent at a high power and would be interceptable. To prevent interception they would have to be sent at a low power level that will not overcome jamming. Antenna directionality, on the other hand, helps defeat both. Directionality at the transmitter helps overcome jamming and reduces interceptability; omnidirectionality at the receive antenna resists jamming and permits the transmitter to use lower power.
5.5.3.4 Terminal Capture
A particular risk of the NCII in the tactical arena is enemy capture of an NCII end user terminal. Palatable solutions to the problem of terminal capture are not obvious and require further investigation. Expensive biometric authentication technology (voice identification, retinal scan, iris scan, fingerprinting, etc.) is available. Alternatively, frequent reauthentication could be required of users at remote terminals. Neither approach appears attractive in tactical circumstances.
Link encryption plus over-the-air-rekeying is not a sufficient answer to this problem. Full-scale network protection requires a number of additional technologies, including firewalls, intruder detection, layered defenses, and so forth. Commercial technology provides limited help in this area. It can supply firewalls, an infrastructure for public key management, key exchange protocols, authenticated routing protocols, and so forth. But at present no commercial technology can adequately deal with the enemy capture problem. DARPA is tackling a wide range of issues with its Information Assurance program, but even so it is unlikely that tactical networks will be sufficiently well-protected in the near to mid term. This should be of significant concern to the Department of the Navy.
5.5.3.5 Lower-layer Tactical Radios
The Department of the Navy employs a wide variety of radios (Open Systems Interconnection (OSI) layers 1 and 2) in its tactical networks. But it also needs lower layers (radios) of the following broad classes:
-
Multiple-access (shared-channel);
-
High-capacity, point-to-point; and
-
Satellite links.
The radios employed for these classes are likely to be unique to the military. At the very least, the Department of the Navy needs anti-jam (AJ) protection for most of its tactical links. In many cases, it is also desirable that the radios have a low probability of interception (LPI) and a low probability of detection (LPD). None of these features are likely to be available in commercial radios to any significant degree.
Encryption is a murkier issue. Traditionally the only encryption used on tactical radios has been link encryption; in essence, all bits sent over the link are encrypted just before transmission and decrypted just after reception. However, end-to-end encryption devices are beginning to enter the commercial marketplace. These devices encrypt a packet at the source computer, keep it encrypted all the way through the network, across multiple links, until it is safely inside the destination computer or destination firewall. Then and only then is it decrypted. Typically these devices use the IP Security (IPSec) protocol suite or vendor-specific protocols and encrypt the contents of datagrams but not their headers. When used for VPNs they can also encrypt a complete datagram and encapsulate it in another datagram wrapper, which hides the encrypted datagram’s header as well as its payload. Since IPSec was designed to handle an open-ended set of encryption mechanisms, it is easy to imagine a type-1 IPSec device. Indeed, such devices may already exist. Tactical networks may benefit from using such an end-to-end encryption strategy. However, this would leave a certain amount of wrapper header in the clear; possibly necessitating an additional layer of link encryption. Needless to say, radio LPI, LPD, and AJ features may also require their own encryption mechanisms. To summarize a complex issue, while it is true that type-1 encryption is needed for the data carried through tactical networks, commercial radios (without embedded cryptos) may suffice for some tactical traffic.
5.5.4 Air Gaps as a Defense
Many believe that for network-centric operations, every network should be connected to every other network. But in fact this may not always be wise. Interconnection brings risk from increased system complexity. It also introduces new weak points for intrusion, interdependencies and, possibly, unintended interactions. An “air gap” (i.e., a physical separation in connectivity) may be necessary in some circumstances. Use of this physical isolation of networks may be preferable in some instances.
Increasing dependence on networked operation can produce greater vulnerability to network intrusion and more serious consequences from such intrusions. Perhaps just as serious is the increased risk of failure propagation because the networks are interconnected. For example, the CEC network is greatly overprovisioned so as to ensure that it is available when needed. It is segregated from other networks so as to eliminate as much as possible any unforeseeable
interference from other systems with the reliability of the CEC network and applications. If this network is interconnected with tactical or other networks, there is considerable unknown risk that CEC applications may not operate correctly when needed.
Similar problems are encountered in safety-critical industries, such as the aviation industry, where the solution traditionally has been to isolate mission-critical functions in their own dedicated computers, networks, and power supplies. Cost pressure to share these resources with other onboard systems is challenging the industry to discover approaches to design safety. This problem is also well known in the telecommunications industry, where undesired feature interaction has been studied intensively. Current understanding of how to build complex systems does not allow guarantees that critical functions such as CEC will operate properly in the dynamic computing environment of the NCII. It may not even be possible to estimate the increased risk that such integration will bring, but this should be attempted and validated to the extent possible before any integration is planned.
5.5.5 Virtual Private Networks
Virtual private networks (VPNs) are a popular technology to allow protected networks to be connected to each other by establishing tunnels through the firewalls that use cryptography to protect the communication from tampering or eavesdropping on the intervening network. Commercial VPNs are not standardized, and many use simplistic key-management schemes that are not secure enough to protect classified traffic or sensitive military traffic. Also, they may not support a large enough number of participating organizations (10 to 100 may be required). In the future, the industry may provide enhancements for supporting security management protocols, for negotiating security policies across administrative domains, and for management tools.
DARPA has created the Dynamic Coalitions program to develop technologies that could improve or replace commercial VPNs. This research will secure the underlying group communication technologies and provide services such as authentication and authorization that are needed for secure collaboration in a coalition environment. One aim is for fast set-up of services as new coalitions or collaborating groups are formed. In addition, DARPA’s new Survivable Network Coalitions program will develop technologies to enable secure collaboration within dynamically established mission-specific coalitions while minimizing potential threats from increased exposure or compromised partners. The program will develop technologies to support the secure creation of dynamic coalitions, including technologies for policy management, secure group communications, and supporting security infrastructure services. Technologies will be developed to dynamically manage and validate operational policy configurations across multiple theaters, securely manage the dissemination of information
within large groups, and augment existing public-key infrastructure technologies to accommodate rapid revocation and cross-certification. These technologies will help coalitions to continue to operate while minimizing potential threats from increased access.
5.5.6 Multilevel Security
The National Security Agency (NSA) Trusted Product Evaluation Program spurred many large vendors of operating systems to build “secure” versions of their systems, most of which were designed to meet the criteria of Class C2 (which does not support multilevel security) of the Trusted Computer System Evaluation Criteria, the so-called Orange Book.11 Some vendors built products to Class B1 (which includes labels but is not strong enough to separate classified information), and a very few vendors built operating systems for Classes B2 and B3, which can be used for protecting classified information where some users are not cleared for the highest levels of information in the system. These systems have not found widespread use within DOD because of their expense (generally in the tens of thousands of dollars per copy), their reliance on specific hardware protections (and thus lack of portability), their lag in features and performance over mainstream technology, and their inability to support popular application software in use in DOD. These operating systems were not popular commercially either, because their conception of security was too narrowly specific to DOD, and the DOD security policy was wired in, meaning that commercial users would have difficulty using these products to enforce their own security policies. Similarly, the NSA Trusted Database Evaluation Criteria resulted in vendor offerings of products with support for labeling of multilevel data at the granularity of rows in a table.12 However, these products rely on operating system support for some of their security, and most have not been ported to the few available high-assurance operating systems (because it would not have been profitable to do so).
It is highly unlikely that we will see high-assurance, multilevel secure (MLS) systems in widespread use in the future. Instead, the computing world will be divided into regions or islands of different classifications, where each island or region operates at system high and holds data that is classified at its system high
|
11 |
Computer Security Center. 1985. Trusted Computer System Evaluation Criteria (DOD 5200.28-STD supersedes CSC-STD-001-83, August 15, 1983). Department of Defense, Fort George G. Meade, Md., December. Available online at <http://www.radium.ncsc.mil/tpep/library/rainbow/5200.28-STD.html>. |
|
12 |
National Computer Security Center. 1991. Trusted Database Management System Interpretation of the Trusted Computer System Evaluation Criteria, NCSC-TG-021. National Security Agency, Fort George G. Meade, Md., April. Available online at <http://www.radium.ncsc.mil/tpep/library/rainbow/NCSC-TG-021.txt>. |
level and lower. However, MLS technologies can be used to interconnect these islands into a system that can exchange information from low islands to high islands. Once low information has entered a high island, it must be treated there as high information, although advisory labels can be used to indicate that the same information is available on low systems elsewhere. Low-assurance MLS technologies (e.g., Orange Book Class B1) can be used to provide such advisory labels, but these technologies are not strong enough to be relied upon to separate data of different classifications with high assurance.
While DOD cannot afford to develop special-purpose multilevel systems for wholesale desktop use, it can afford to develop specialized security technology to interconnect different classification islands and to approach MLS capabilities. A few such technologies have been developed. Starlight is an Australian-developed system that allows a computer monitor and keyboard to be switched from one system high network to another, giving an approximation to desktop MLS processing. The NRL pump is a system that can reliably transport data from low networks into high networks without leaking any high information back into the low network. Secure Information Through Replicated Architecture (SINTRA) is a system developed by NRL that creates the functionality of an MLS database by linking system-high databases in different classification islands in a way that does not leak information. Software Architecture and Logic for Secure Cooperative Applications (SALSA), a similar idea for MLS workflows, was also developed by NRL.
Encryption can also be used for high-assurance separation of information of different classification. It has long been used by DOD in communications networks to provide secure separation of communications of different classifications on a common physical network. Commercial networks, including commercial satellite networks, can be used for carrying multilevel data, since the data are separated by cryptographic means. (However, the use of commercial networks permits vulnerability to denial-of-service attacks and traffic analysis.)
The idea of cryptographic separation can be extended into information repository systems. Yet this does not solve the multilevel security problem, because within a processor, information must be decrypted for processing, so that additional strong controls are needed to prevent leakage of unencrypted high data to low processes or users. Moreover, this approach is not popular commercially for reasons of cost and ease of use.
True multilevel security capabilities, other than networks shared through cryptographic separation, barely exist in the Department of the Navy and in the DOD. However, the NRL pump and the Australian Starlight system are promising for future multilevel processing needs, as are SINTRA and SALSA. NRL should be tasked to develop these and other promising near-term technologies to the point where they are ready for widespread introduction into the Navy Department and for use with a wide variety of technologies.
5.5.7 Traffic Analysis
An adversary may be able to perform traffic analysis to identify critical nodes and bottlenecks and may develop attacks on these points, or it may infer information about naval operations and plans. NRL has developed a technique called onion routing to provide some protection against traffic analysis. It should continue to pursue this and other means of protection against traffic analysis. It should grow these technologies and promote their use within the Department of the Navy.
5.5.8 Other Issues
There is a critical shortage of information assurance expertise both within the Department of the Navy and in the nation at large. The Navy Department should encourage the government to expand the information assurance skill base, perhaps through educational programs sponsored by the National Science Foundation (NSF). Such programs could help produce the naval personnel of the future who will be responsible for maintaining the security of the NCII. There is also a shortage today of good minds working on security research. An investment in research by NSF at universities into the fundamentals of computer security and other areas related to information assurance would begin to produce a new generation of researchers and help to gain a greater degree of academic acceptability for the field. Even so, it is not clear whether progress will be rapid enough to keep up with the threats and vulnerabilities introduced by new technologies.
Information assurance is not receiving appropriate attention at high enough levels within the Department of the Navy. While NRL is developing many promising technical solutions, it is having difficulty getting attention within the Navy Department for the work. The concerns it reports to offices such as N6 get diluted by many other issues. Responsibility for information assurance must be made a key priority and assigned at a high level within the Navy Department. This would ensure that NRL and other naval information assurance research receive adequate resources and that the new technologies will be implemented. It would also create a focal point within the Department of the Navy with sufficient authority to develop and deploy methodologies and tools for assessment and compliance.
Dependability is another requirement of critical naval systems. Redundancy is the standard means for achieving dependability, but it is an expensive approach and provides no protection for correlated failures and little protection for software failures. Like security, dependability is not part of the readiness assessment. Additional near-term measures could include increased continuous monitoring and testing of systems. Most importantly, naval forces should plan
ways of operating when there are security and dependability failures, such as outages or service degradation.
Security and dependability should also be an explicit part of the spiral development model discussed in Chapter 2. First, security and dependability should be designed into new technologies so that vulnerabilities can be identified early and corrected in subsequent designs. Red teaming should be an integral component of the spiral development experiments. Second, there should be security and dependability dimensions of experiments that are carried out as part of the spiral process. It is important that the new alternative doctrine, operational concepts, and tactics explored in these experiments take into account the security and dependability characteristics of the technologies. To allow informed choices, it is important that these experiments mimic the hypothesized weaknesses of the technologies, so that strategies can be developed to deal with unavailabilities, degraded capabilities, or misbehaviors due to security or dependability failures.
The necessary protections for the NCII will not be inexpensive to procure, install, maintain, and keep current. In addition to the costs of the technology will be the costs of developing and enforcing essential policies and procedures, especially because there are currently no adequate technical solutions for many aspects of the information assurance problem. Ongoing programs for security awareness and training will also help to keep naval personnel vigilant about noticing and reporting suspicious behavior of their systems. The Department of the Navy can expect to spend at least 5 percent of its budget for information technology (IT), IT maintenance, and IT training on information assurance. Note that industry typically spends about 5 percent of its IT budgets on security, while the U.S. government spends less.
5.6 RESEARCH PRODUCTS SUITABLE FOR NEAR-TERM APPLICATION
In recent years, DARPA and other agencies have funded much promising research in information assurance. This research has produced some promising near-term technologies that the Department of the Navy should evaluate and exploit to the extent possible. Because of its unique expertise in information assurance and its capabilities for technology evaluation and development, NRL should be tasked to mature the most promising and applicable of these and to make them ready for deployment. Examples include encrypted e-mail, secured protocols, better intrusion detection components, digital signatures on software, and security wrappers. Once these technologies have been made ready by NRL, the Navy Department must then help to deploy them throughout the organization. NRL could also be charged with monitoring the state of the art within the Department of the Navy for security and dependability technologies and procedures, this information then being disseminated throughout the Navy Department.
DARPA’s Information Survivability program,13 which finished in 1999, is a good source of technologies that NRL could consider experimenting with. These technologies include early prototypes of hardened network services, early versions of wrapper generation tool kits, prototype local intrusion detectors, and a framework for coordination of intrusion detection and response. The program is divided into four areas. Examples of research results emerging from these four areas that could be considered by NRL are summarized in Table 5.1.
In addition, the DARPA Information Assurance program has taken many of the DARPA Information Survivability technologies in prevention, detection and response, and security management for C4I information systems and has integrated them into a security architecture that, while integrating security and survivability concepts, techniques, and mechanisms, will also provide interfaces for future security upgrades. Access control technologies that have been integrated into the architecture include encryption of message traffic and firewalls. Other solutions include policy-controlled automated security guards and release stations, strong user authentication, and protected execution domains to limit damage from certain types of attack. Intrusion detection and response capabilities have also been integrated into the architecture. In addition, a security management function is being integrated into the architecture. NRL could evaluate and mature portions of this security architecture for possible use within the Department of the Navy.
This collection of research results includes specific prototype technologies that address portions of the Department of the Navy’s technical information assurance problems. Most of these technologies (specifically network security technologies, secure computing platforms, and wrapper technologies to embed security functionality into legacy systems) fall into the protection category. Several technologies fall into the detection category. There are few, if any, technologies for the tolerance component of defense in depth. There is the beginning of a security architecture to tie many of these elements together in a standard way. By maturing and deploying selected technologies from this set as well as from other technologies being developed elsewhere, the Department of the Navy can accelerate the application of appropriate technical solutions to aspects of its information assurance problem.
|
13 |
See Footnote 5. |
TABLE 5.1 Technologies from the DARPA Information Survivability Program to Consider for Near-term Application
|
Problem |
Technology |
Description |
|
Secure Networking |
|
|
|
Internet routing infrastructure is subject to denial-of-service attacks. |
Secure open shortest path first (OSPF) routing protocol Nimrod routing security |
Authentication added to routing |
|
Internet naming and addressing infrastructure is vulnerable to denial-of-service attacks. |
Internet Protocol (IP) version 6 (IPv6, also known as IPSec) prototype |
Encrypts IP packets |
|
|
Secure domain name service (DNS) protocol |
Adds authentication and authorization to DNS |
|
Network security services are not easily integrated into applications. |
Cryptographic application programming interfaces |
Give programmers standard ways of adding security functionality to software |
|
|
Simple public-key interface |
|
|
|
Key management interfaces |
|
|
Network security services are not interoperable. |
IPSec key agreement protocol |
Multilayer security negotiation protocol |
|
|
Secure mobile IP |
Preserves user identity for nomadic users traveling across different networks |
|
Encrypting group communication and managing membership changes are not scalable to large groups. |
Secure fault-tolerant group communication |
Scalable algorithms for key management and membership revocation, and language for specifying group communication policies |
|
Secure Computing Platforms |
|
|
|
Traditional operating system security is inappropriate for modern networked environments with complex policies. |
Domain-type enforcement “compiler” |
Fine-grain access control and an associated policy |
|
Adequate security is available only in special-purpose operating systems with tiny markets. |
Fluke operating system |
Enables integrating security into commercially viable next-generation operating systems |
|
Problem |
Technology |
Description |
|
Distributed systems meeting more than one critical property are beyond the state of the art. |
Horus distributed computing system |
Group communications system supporting secure, real-time fault tolerance |
|
Secure Computing Platforms |
|
|
|
Rigid security and firewalls inhibit tightly coupled cross-domain applications and establishment of temporary security associations. |
Adage authorization server |
A distributed authorization server and policy language |
|
Sigma security middleware |
Propagation of access control information across enclave boundaries |
|
|
Detection and Tolerance |
|
|
|
Current intrusion detection techniques are limited to detecting a small set of well-known events. |
Emerald intrusion detection system |
Detects unknown attack types on networks |
|
Current detection techniques do not scale and do not support automated response. |
GRIDS intrusion detection system |
Allows attacks to be specified as a graph across a network, thus allowing detection of larger-scale attacks |
|
|
Intrusion detection and isolation protocol (IDIP) |
Allows coordinated detection and automated response |
|
Current technology does not support incident response, which is a costly, labor-intensive process. |
Diagnosis, explanation, and recovery from computer break-ins |
Analyzes a system for indicators of an intrusion; explains to the system administrator what it found, what it probably means, and how to recover |
|
Lack of standards impedes adoption of even current technology. |
Common intrusion detection framework |
Establishes standard interfaces for event generators (sensors) and analysis engines (detectors) |
|
Current intrusion detection detects attacks on isolated machines, not attacks on the network infrastructure. |
JiNao intrusion detection system |
Detects intruders in network routers, switches, and network management channels; integrated with network management and has reconfiguration capabilities |
|
Problem |
Technology |
Description |
|
Multicast group communication protocols are vulnerable to malicious participants. |
Secure group and secure ring protocols |
Group communication protocols that can prevent a malicious processor from disrupting the correct delivery of messages and from conducting successful denial-of-service attacks |
|
Common programming errors leave most systems vulnerable to buffer overflow attacks, the most common type of attack on the Internet. |
StackGuard compiler |
Reduces vulnerability to buffer overflow attacks; no source code changes required; executables are binary-compatible with existing operating systems and libraries |
|
Wrappers |
|
|
|
Commercial products introduce unreliability and security risks. |
Generic security wrappers |
Wrapper technology to augment legacy and commercial off-the-shelf components with security functionality; includes a wrapper specification language and a kernel-resident wrapper system; intercepts system calls to control privileged and nonprivileged programs; demonstrations include control of administrative privileges, access control, and encryption |
|
Integrators cannot assemble components and wrappers into a trustworthy whole. |
Composable replaceable security modules |
A tool to build security into systems by assembling security functions from a library of reusable, plugable security modules, with standard functionality and interfaces |
|
Vulnerability/resistance of a product or system requires evaluation. |
Vulnerability assessment tool |
White-box security evaluation tool locates vulnerable points in source code, using realistic attack models and taxonomies of known security flaws |
5.7 INFORMATION ASSURANCE RESEARCH
Because there is a large shortfall of security technologies relative to naval needs, the Department of the Navy must be an advocate within the DOD for long-term research in several areas not being addressed by industry:
-
Technologies for intrusion assessment to distinguish serious targeted attacks on critical systems from attacks on systems of lesser concern;
-
Technologies for intrusion-tolerant systems, to maximize a critical system’s ability to keep on providing service despite successful attack and partial system compromise;
-
Technologies to limit an attacker’s ability to carry out denial-of-service attacks; and
-
Technologies to allow existing and legacy systems to be retrofitted with some security and reliability functionality.
Research is also needed in mobile code security, extending the capabilities of virtual private networks, and dependability.
There is, as well, a need to develop DOD-specific solutions for areas that industry is not addressing because there are no common commercial analogues, particularly in tactical networking. One risk faced by NCII in the tactical arena is that of enemy capture of an NCII end user terminal. Palatable solutions to this are not obvious and require further investigation.
5.7.1 Intrusion Assessment
Once local intrusion detectors are widely employed, it will become possible to make use of their collective outputs to try to gain a picture of the overall situation for the NCII. The aim of intrusion assessment is to distinguish serious targeted attacks on critical systems from attacks of lesser concern. This function takes reports from an infrastructure of intrusion detectors as inputs. The idea is to infer probable specific intent to carry out a particular hostile course of action for some specific purpose. This might be accomplished by correlating and analyzing observed or reported events in a way similar to the fusion of intelligence data (Figure 5.3).
When an attack is detected, it is useful to determine its mission impact as well as the potential mission impact of employing a given countermeasure (which may involve closing some connections for a time). To facilitate this, it might be useful for the common operational picture (COP) to include the NCII’s computing and networking assets (links, nodes, and critical processes). Then an information assurance analyst could be given access to an appropriate COP to assess alternative courses of actions and plan actions.
For all this to be possible, the quality of the technology for detecting local

FIGURE 5.3 Fusion of intrusion detection.
intrusions must be greatly improved. The state of the art is illustrated by the following example. In a 2-week period, Air Force Information Warfare Center’s (AFIWC’s) intrusion detectors at 100 Air Force bases alarmed on 2 million sessions. Manual review reduced these to 12,000 suspicious events. Further manual review reduced them to four actual incidents. Almost every reported event is a false alarm or a trivial incident such as a failed password, and performing intrusion assessment from these alarms over all Air Force bases is a manual and laborious procedure involving hundreds of staff. Intrusion assessment technology should aim for intelligent filtering of events plus automated analysis requiring at most a handful of staff at a DOD reporting center or security anchor desk. Also, the current assessment task is limited to compiling statistics on the frequency of various types of attack, and it is not possible to obtain meaningful, specific, predictive information from this manual analysis.
The number of false alarms in local detectors may be reduced by developing better sensors. The sensors in use today are of two types: operating system audit trails and network sniffers. Both gather far more data than is necessary and omit data that may predict hostile activity. False alarms may be also reduced by adding a capability for peer-to-peer cooperation among local intrusion detectors, so that some limited assessment can be performed among a set of cooperating detectors covering a given region and events of only local concern can be suppressed from being reported to a central point. In support of this, detection components will need the ability to discover each other, negotiate requirements, and collaborate on diagnosis and response.
In addition, the detection technologies must be capable of detecting known attacks with high confidence and unknown attacks with reasonable confidence. The techniques must have very low false alarm rates, especially when they are used in very large systems, and must themselves tolerate missing, incomplete, untimely, or otherwise faulty data.
To analyze a collection of intrusion reports so as to identify specific, imminent, hostile activities of high consequence, it is necessary to infer the intent of hypothesized attackers. It may be possible to use automated planning and plan recognition technology to hypothesize goals for information warfare adversaries, develop plans for accomplishing each goal, and recognize when a plan is being carried out. Analysis techniques to be used at various reporting levels may include report correlation, automatic pattern detection, event classification,
FIGURE 5.4 Network of intrusion detectors and reporting centers.
model-based reasoning to infer intent and predict future status, effect correlation to assess damage, and evidential reasoning to assess certainty.
Figure 5.4 shows a network of intrusion detectors and reporting centers. The reporting centers are organized roughly into layers, with the local detectors reporting into organizational security centers, which in turn report into regional reporting centers, which report into DOD and National reporting centers. At each layer of this network there would be a security detection and response center, which would have a number of functions (see Figure 5.5). The detection function analyzes and filters events reported from lower layers. The analysis is to find items of interest to this layer as well as items for reporting to higher layers. The assessment function attempts to understand coordinated events of interest to this layer and for reporting to higher layers. The tracing function can initiate tracebacks to attempt to discover the source of an event, or may participate in tracebacks initiated by other centers. The event notification function notifies peers or lower layers of hostile events happening elsewhere so they can prepare a defense. The automated response function can initiate local actions or instruct lower layers to take specific recommended actions to thwart a suspected in-progress attack or to implement specific defensive actions. This function can also exchange information with its peers to help decide what actions to take or to recommend to lower layers.
DARPA is beginning to invest in this area with its three new programs: Strategic Intrusion Assessment, Cyber Command and Control, and Autonomic
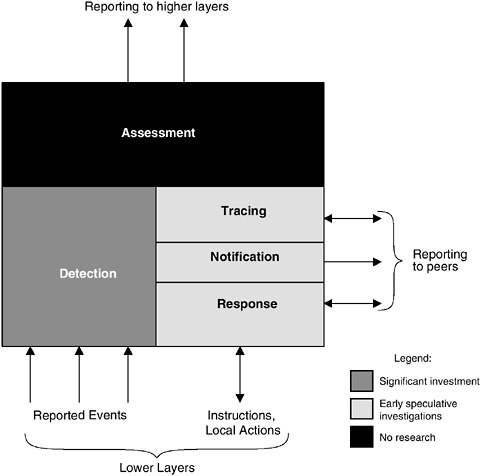
FIGURE 5.5 Security detection and response center.
Information Assurance. The Strategic Intrusion Assessment program aims to develop technologies capable of distinguishing significant patterns of events that cross geographic and administrative domains and that indicate a possible information warfare threat. It will develop a capability for peer-to-peer cooperation among detectors, including the ability for detectors to discover each other, negotiate requirements, and collaborate on diagnosis and response. The program will also develop techniques for correlating the output of intrusion detectors to infer the intent of the attacker. The Cyber Command and Control program will develop decision support tools to allow humans to assess the security status of a command and control system. It will assist human beings in ascertaining the activities and goals of adversaries attacking the system and in determining and carrying out the courses of action to counter them that are most
effective and that interfere least with the system’s ability to carry out its operational functions. The Autonomic Information Assurance program will develop technologies to allow systems to encode tactics to automatically detect and respond to routine known attacks so that the decision makers can focus on the strategic situation. The program will develop approaches for fast, adaptive defenses against these types of attacks. This should result in the ability to prevent damage from large classes of previously known attacks.
5.7.2 Intrusion Tolerance
Intrusion tolerance aims to ensure the continued correct operation of the surviving portion of a system even when it has been partially compromised. Component technologies include the ability to rapidly recognize corrupted data and programs, intrusion detection to recognize a local attack, techniques to constrain an attacker’s resource consumption so as to minimize its opportunity to deny service, resource allocation methods to assign the most important tasks to the remaining resources, and methods to automatically repair damaged processes.
Traditional system designs have “central nervous systems” that, if attacked, can completely disable the system. Corrupted or malicious member entities can lead to incorrect functioning of the system as a whole. A possible architecture for an intrusion-tolerant system is one that is highly decentralized, so that the attacker cannot cripple the entire system by attacking one or a few points. The system could comprise many relatively independent processes that are collaborating to achieve a common goal. In highly decentralized systems, the overall behavior is the result of many small decisions made autonomously by member entities. One example of such a system is the Federal Aviation Administration free-flight air traffic control system currently being developed, in which individual aircraft will be able to negotiate with one another for their desired airspace rather than being controlled centrally from the ground. The Internet is another example of a system in which individual entities act autonomously yet collectively provide a global function. Such systems are inherently survivable in that a subset of the entities may be corrupted or lost and the overall system can continue to carry out its global function. (Note that if decentralized control is deemed to be too costly for routine system operation, the system can be designed to switch from centralized to decentralized operation when a threat is detected, and various degrees of decentralization may be designed in.) Protocols among the individual entities can allow them to cooperate to detect and isolate corrupted or malicious member entities. Survivability can be strengthened by the use of artificial diversity techniques, so that no single attack type can disable a large fraction of the processing entities. The system should be capable of self-monitoring, so that it can ensure that the most critical tasks get access to the uncorrupted resources. Self-monitoring can also recognize and trigger appropriate action when the collection of local responses results in some undesired
system-level behavior. This collection of strategies can make systems inherently resistant to attack, much as the immune system makes humans resistant to disease. These defenses limit the spread or impact of an attack.
Intrusion tolerance requires an intrusion detection and response capability. This in turn requires targeted and possibly redeployable sensors to perform security monitoring; an infrastructure of intrusion detectors that performs analysis on data collected by the sensors; and response elements capable of reacting to alerts issued by the detectors to isolate the attacker, assess the damage, and recover.
Economic forces are driving out computational diversity. Market forces and consolidation within the computer industry have resulted in a few major brands of software and hardware being ubiquitous. The NCII will also be largely homogeneous, with common products in use everywhere. Such homogeneity leads to widespread common vulnerabilities that can be exploited by common attacks. DARPA is beginning to investigate means of artificially introducing diversity into homogeneous systems. Introducing diversity into highly decentralized systems can limit the subpopulation susceptible to any given attack and can cause attacks to have only local effects or to die out before they spread widely. Diversity is also a hedge against unanticipated means of attack; at least some system elements will survive and provide a basis for reconstitution. Means under investigation for artificially introducing diversity include self-specializing software that could reconfigure itself for a new specialization in response to attack; compilers that could vary the location of buffers, data structures, and code sequences, making attacks against them nonrepeatable; and multiple diverse implementations of the same functions.
Executing processes may fail or behave incorrectly owing to a corrupted program state. Individual processes in a survivable system should be able to detect and repair a corrupt program state so as to tolerate attack and maximize their running lifetime. Processes could check on their own integrity, send out alarms, and restore themselves to a safe state. For example, they could repair dangling pointers, change variable values to maintain invariants, restart failed connections, purge filled buffers, resynchronize with other processes, close unresponsive wait states, restore to a good checkpoint, and reload code or data from disk.
DARPA’s new Intrusion Tolerant Systems program is investigating innovative designs for decentralized systems that are inherently resistant to attack. The research will continue and build on research into artificial diversity techniques that were initially investigated in DARPA’s Information Survivability program. It will also develop methods to enable member entities to detect and isolate corrupt entities. Survivable resource allocation methods are being developed to assign surviving resources to the most critical functions so as to allow damaged systems to continue functioning despite the loss of significant resources and even of critical centralized control functions. Monitoring approaches are being
developed to give systems the ability to monitor global behavior and to take local action to prevent undesired emergent effects. Integrity techniques are being developed to allow continued correct operation of the surviving portion of the system even when an attack has compromised data and code. These will include techniques to rapidly distinguish intact from corrupted information after penetration, to protect mobile code from corruption, and to maintain the integrity of systems in the presence of attack.
5.7.3 Preventing Denial of Service
Attacks that consume system resources or make them unavailable to the legitimate users and processes of the system are known as denial-of-service attacks. These attacks waste system resources and can exhaust them. They can cripple network elements and disrupt network operation. For example, Internet routing protocols commonly in use today have vulnerabilities that allow malicious entities to spoof router table updates. This could result in the propagation of bad routing information throughout the network, with consequences ranging from poor network performance, through the inability to deliver messages to certain destinations, to the collapse of portions of the network. Similar attacks on the Internet domain name service could make the network unable to deliver messages. Attackers also could take advantage of high-cost protocol checks (such as authentication) to consume resources.
Denial-of-service attacks can be thwarted by constraining an attacker’s consumption of resources. Techniques are needed that would constrain denial-of-service attackers to a small percentage of system resources and that would slow such attacks sufficiently so that they can be detected.
DARPA has announced the new Fault Tolerant Network (FTN) program14 to develop focused technologies that support continued operation in the presence of successful attacks. The program will address in particular the vulnerabilities and issues expected to arise in the highly networked environments envisioned for future warfighting operations.
Many network services represent potential points of failure. The FTN program will apply fault tolerance ideas to network services to reduce the amount of damage sustained during an attack and to enable continuous correct service delivery even when the services are under successful attack. This should help ensure continued availability and provide a technical basis for graceful degradation of service under successful attack, as well as help maximize the residual capacity available to legitimate users.
5.7.4 Hardening Legacy Systems
Naval systems contain a high percentage of legacy and off-the-shelf components that do not provide the properties needed for information survivability. Methodologies are needed to allow the insertion of security functionality into legacy systems to address the vulnerabilities of the large in-place legacy base, which will persist for years to come. Also, because commercial products will not have the security and survivability features required for critical naval applications, a means is needed to allow designers to selectively harden such products.
The concept of security wrappers appears promising for retrofitting some security functionality into legacy systems. Wrappers encapsulate an existing component by intercepting all input to and output from the component (see Figure 5.6). This is done so as to require little or, ideally, no change to the wrapped component or to the components that interact with it. Indeed, the wrapped component, as well as those components with which it interacts, will be unaware of the wrapper. The wrapper interposes additional security and survivability functionality. For example, a wrapper may be added to create a security log, which may be analyzed by a separate intrusion detector. Or, wrappers on sending and receiving components can perform encryption/decryption or message integrity checks. As another example, a wrapper can be used to perform access control by filtering access requests to a component. To add fault tolerance, a wrapper could transparently replicate a component.
A number of security and survivability functions, such as encryption, access control, security monitoring, message integrity, management and control, and replication, could be provided by wrappers. These basic functions could be implemented in reusable building blocks that could be automatically provided by a wrapper generator according to a wrapper specification. The building blocks might come in several varieties for the same function; for example, there might be several implementations of authentication (passwords, secure ID, Kerberos, Fortezza, and so on), each with different specified strengths and costs. A wrapper specification could provide requirements for strength of mechanisms and constraints on their costs. Such modularity would also lend itself to future upgrading to stronger mechanisms without having to completely reconstruct the wrappers.
A significant research challenge is to provide some assurance that the wrappers cannot be bypassed. Another challenge is to develop a methodology that would allow an integrator to predict the security and survivability characteristics of components and wrappers, as well as tools to assist an integrator in assembling components and wrappers in a trustworthy manner.
The DARPA Information Survivability program has investigated the use of wrappers for security and survivability and has funded a collection of security wrapper projects that are developing tool kits that allow a developer to automatically generate security wrappers from a set of wrapper specifications.
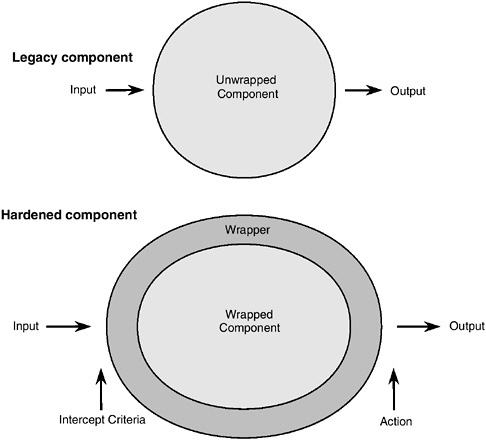
FIGURE 5.6 Concept of security wrappers.
SOURCE: Developed from information in Oostendorp, Karen A., Christopher D. Vance, Kelly C. Djahandari, Benjamin L. Uecker, and Lee Badger. 1997. Preliminary Wrapper Definition Language Specification, TIS Report No. 0684, Trusted Information Systems, Inc., Glenwood, Md.
5.7.5 Mobile Code Security
In the future, mobile code is expected to be used to deploy new services quickly and cheaply. While there are obvious security challenges inherent in doing this, commercial systems such as Java are rapidly developing many of the necessary security underpinnings for such uses. Continued attention is required to ensure that such security mechanisms are adequate.
Mobile code could also be used to more easily deploy new security functionality, as well as to upgrade existing functionality. This will make it easier to evolve and maintain systems. Active networking technology being developed
by DARPA will extend similar capabilities to the network, resulting in networks that are extensible. For example, network functionality could be added to log events so that intruders can later be tracked, or to choose routes based on security considerations. To enable future naval uses of such technology, continued research is needed in mobile code security.
5.7.6 Dependability
While hardware dependability is a fairly well-understood science, this is not the case for software dependability. Software can have numerous bugs, and systems with large software components frequently fail, lock up, suffer unexplainable performance degradations, and can loose data. Dependability methods for hardware do not work for software, for many reasons. Hardware faults are often the result of parts wearing out or are due to random effects such as stray radiation. Since these types of faults tend to be independent, in that failure in one part does not affect the likelihood of failure in another part, failure models can be developed for commonly used hardware components to predict such characteristics as mean time to failure. The independence of the faults makes the use of redundant hardware components an effective fault tolerance strategy.
Software does not share these characteristics of hardware. It does not wear out. The causes for failure come from the humans who designed and wrote it. Failures cannot be assumed to be independent, especially because many copies of the same software are used in a system, but also because it is likely that different software developers will make the same kinds of errors. This makes it is very difficult to use redundancy as a means of software fault tolerance. Detection of and recovery from software faults is a research area that is not receiving much funding in the United States. Much of the research is motivated by the need to build ultracritical systems whose failure has very costly consequences, such as nuclear power generation, flight control, or air traffic control. Solutions that are acceptable for such systems are generally too costly for less critical systems, such as command and control systems. This means that designers of most of the large-scale computing systems in use today must use ad hoc means of obtaining reliability in those systems.
5.8 RECOMMENDATIONS
While a technical solution for the information assurance problem does not seem possible in the foreseeable future, the benefits to be gained from network-centric operations nonetheless make such operations imperative. A program of vigilance, testing, and continuing information assurance research will therefore be required. The committee recommends as follows:
Recommendation: The Department of the Navy should endeavor to use all available technologies to secure the NCII.
NRL could be tasked to help the Department of the Navy maintain an awareness of available technologies and also to follow in-progress research and select promising new technologies to develop and disseminate throughout the Department of the Navy. Earlier in this chapter in section 5.6, the committee identifies possible near-term technologies for consideration.
Recommendation: The Department of the Navy should take steps to ensure that systems are continuously maintained in a secure state.
Even with suitable technologies installed, continuous effort is required to maintain systems in a secure state. This can be accomplished by a combination of technical and procedural means, including regular internal use of red teams to test system configurations. System managers must keep up to date with the latest patches, fixes, and recommended configurations. A central source of this information within the Department of the Navy would help with this effort.
Recommendation: The Department of the Navy should take steps to increase and maintain security at all levels of personnel.
Red teaming exercises are valuable as a security awareness tool, especially to bring security to the attention of management. In addition, all naval personnel should be made aware of and trained in information assurance.
Recommendation: In designing the NCII, the Department of the Navy should use a defense-in-depth strategy to address unknown vulnerabilities.
In designing the NCII, it is not safe to take a risk management approach that assumes that all system vulnerabilities can be discovered and thereby will provide a basis for protection strategy. Instead, all components must be treated as vulnerable, including any protection mechanisms. Layered protection and a defense-in-depth strategy are required. Procedural and physical security measures should be developed to further reduce the risk where the available technology is not adequate.
Recommendation: The NCII should be designed to address security and assurance for tactical links.
Although cryptography makes spoofing difficult, attention must be paid in the tactical portion of the NCII to reducing the hazards arising from an adversary’s capture of equipment, to providing a way to incorporate coalition
partners in the NCII, and to defeating traffic analysis. The roles of spread spectrum and directional antennas in defeating jamming and interception are well understood, but existing spread-spectrum devices and multibeam directional antennas are expensive. In the near term, programmable modular radios should be programmed to adapt their waveforms and data rate to instantaneous jamming conditions. In the long term, affordable, high-gain, multibeam antennas should be sought.
Recommendation: The CNO and the CMC should take steps to ensure that fleet and Marine training encompasses situations with impaired information and NCII functionality, and that fallback positions and capabilities are prepared to meet such eventualities.
Network-centric operations will depend for their success on the correct functioning of the NCII. But NCII functionality may deteriorate or malfunction or be unavailable due to attack or failure. Because it is likely there will be attack on the NCII, it is imperative that naval forces train for situations with impaired NCII function. By this the committee means not only that the system staff should train to quickly restore service, it also means that operational forces should train to deal with system failure situations. The Department of the Navy has a tradition of developing operational workarounds for loss or degradation of radio frequency communications in tactical operations. The same should be done for the NCII. Without this, naval forces will be unprepared to deal with these situations, which are likely to arise.
Recommendation: When mission-critical networks and functions are considered for interconnection, the Department of the Navy should weigh the risks against the benefits.
A prominent feature of the NCII is its ability to connect disparate networks and functions. The NCII designers should recognize that while this brings great benefit, it also brings risks. When mission-critical networks and functions are considered for connection, it is essential to weigh the risks against the benefits. For example, certain functions may be considered so critical that any risk to their timely and correct functioning during a crisis is intolerable. In such cases, the decision may be to not connect, and to use an air-gap defense.
Recommendation: The Secretary of the Navy, the CNO, and the CMC should assign responsibility for information assurance at a high enough level within the Navy and the Marine Corps, and with sufficient emphasis, to ensure that adequate and integrated attention is paid to all aspects of this problem in the design and operation of the NCII.
Information assurance is not receiving appropriate attention at high levels within the Department of the Navy. Currently no single individual within the Department of the Navy has this responsibility and authority.
Recommendation: The Department of the Navy should push for research to address its critical NCII information assurance needs.
Because there is a large shortfall of current security technologies relative to naval needs, the Department of the Navy must be an advocate within the DOD for long-term research in several areas not being addressed by industry, including intrusion assessment, intrusion-tolerant systems, prevention of denial of service, approaches to retrofitting legacy systems with some security and reliability functionality, mobile code security, extending the capabilities of virtual private networks, and dependability. There is also a need to develop DOD-specific solutions for areas that industry is not addressing because there are no common commercial analogues, particularly in tactical networking.












































